Download Overview of Cryptographic Techniques and more Lecture notes Cryptography and System Security in PDF only on Docsity!
Overview of Cryptographic
Techniques
Some Basic Terminology
• plaintext - original message
• ciphertext - coded message
• cipher - algorithm for transforming plaintext to ciphertext
• key - info used in cipher known only to sender/receiver
• encipher (encrypt) - converting plaintext to ciphertext
• decipher (decrypt) - recovering ciphertext from plaintext
• cryptography - study of encryption principles/methods
• cryptanalysis (codebreaking) - study of principles/
methods of deciphering ciphertext without knowing key
• cryptology - field of both cryptography and cryptanalysis
Characteristics of Cryptographic Characteristics of Cryptographic
Techniques Techniques
- (^) Classified along three independent dimensions:
- (^) The type of operations used for transforming plaintext
to ciphertext
- (^) The number of keys used
- (^) symmetric (single key)
- (^) asymmetric (two-keys, or public-key encryption)
- (^) The way in which the plaintext is processed
Symmetric Encryption
• or conventional / private-key / single-key
• sender and recipient share a common key
• all classical encryption algorithms are
private-key
Requirements
• two requirements for secure use of
symmetric encryption:
– a strong encryption algorithm
– a secret key known only to sender / receiver
• mathematically have:
Y = E K ( X ) [= E(K, X ) ]
X = D K ( Y ) [= D(K, Y ) ]
• assume encryption algorithm is known
• implies a secure channel to distribute key
Brute Force Search
• always possible to simply try every key
• most basic attack, proportional to key size
• assume either know / recognize plaintext
Key Size (bits) Number of Alternative Keys Time required at 1 decryption/ μ s Time required at 10^6 decryptions/ μ s 32 232 = 4.3 109 231 μs = 35.8 minutes 2.15 milliseconds 56 256 = 7.2 1016 255 μs = 1142 years 10.01 hours 128 2128 = 3.4 1038 2127 μs = 5.4 1024 years 5.4 1018 years 168 2168 = 3.7 1050 2167 μs = 5.9 1036 years 5.9 1030 years 26 characters (permutation) 26! = 4 1026 2 1026 μs = 6.4 1012 years 6.4 106 years
Caesar Cipher
• earliest known substitution cipher
• by Julius Caesar
• first attested use in military affairs
• replaces each letter by 3rd letter after
• example:
meet me after the toga party
PHHW PH DIWHU WKH WRJD SDUWB
Caesar Cipher
• can define transformation as:
a b c d e f g h i j k l m n o p q r s t u v w x y z
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
• mathematically give each letter a number
a b c d e f g h i j k l m n o p q r s t u v w x y z 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
• then have Caesar cipher as:
c = E( p ) = ( p + k ) mod (26)
p = D(c) = (c – k ) mod (26)
Playfair Cipher
• not even the large number of keys in a
monoalphabetic cipher provides security
• one approach to improving security was to
encrypt multiple letters
• the Playfair Cipher is an example
• invented by Charles Wheatstone in 1854,
but named after his friend Baron Playfair
Playfair Key Matrix
• a 5X5 matrix of letters based on a keyword
• fill in letters of keyword (minus duplicates)
• fill rest of matrix with other letters
• eg. using the keyword MONARCHY
M O N A R C H Y B D E F G I/J K L P Q S T U V W X Z
Polyalphabetic Ciphers
• polyalphabetic substitution ciphers
• A set of related monoalphabetic substitution rules is used
• use a key to select which alphabet is used for each letter
of the message
• use each alphabet in turn
• repeat from start after end of key is reached
• make cryptanalysis harder with more alphabets to guess
and flatter frequency distribution
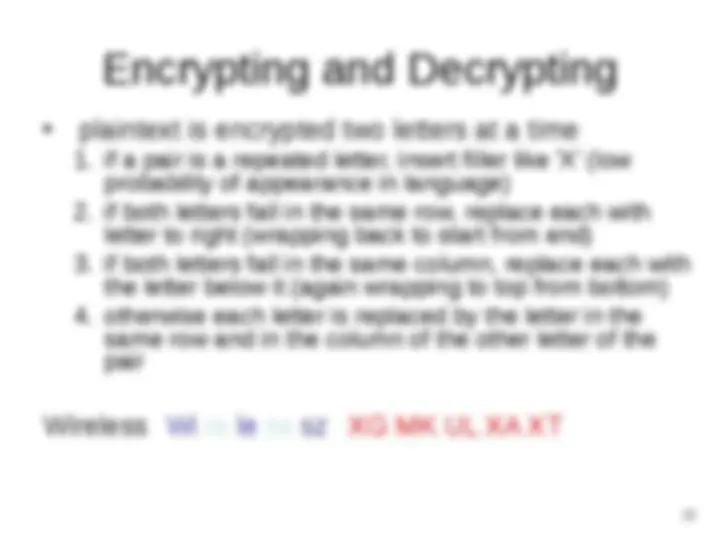
Key: deceptive 3 4 2 4 15 19 8 21 4
plaintext: wireless 22 8 17 4 11 4 18 18
ciphertext: zmtiaxao 25 12 19 8 26 23 26 39
Vigenère Cipher
• simplest polyalphabetic substitution cipher
• effectively multiple caesar ciphers
• key is multiple letters long K = k
1 k 2 ... kd
• ith^ letter specifies ith^ alphabet to use
• use each alphabet in turn
• repeat from start after d letters in message
• decryption simply works in reverse
Vernam Cipher and One-time
Pad
• Keyword is as long as the plaintext and
has no statistical relationship to it.
• Vernam system works on binary data with
ith bit of text exclusive ored with ith bit of
key to produce ith bit of cipher
• In one one-time pad key is used only once
• This scheme is unbreakable
Transposition Cipher
• Mapping is performed by some sort of
permutation on the plaintext letters.
• Example: Rail fence of depth 2
text : meet me after the toga party
m e m a t r h t g p r y
e t e f e t e o a a t
cipher: MEMATRHTGPRYETEFETEOAAT
Rail fence of depth 2