


















Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
this are my study materials for website design and security
Typology: Summaries
1 / 39

This page cannot be seen from the preview
Don't miss anything!
































KCIC
PRESENTER: Ms JIJILIN CRIMSON
KCIC
Search Field
Search Field
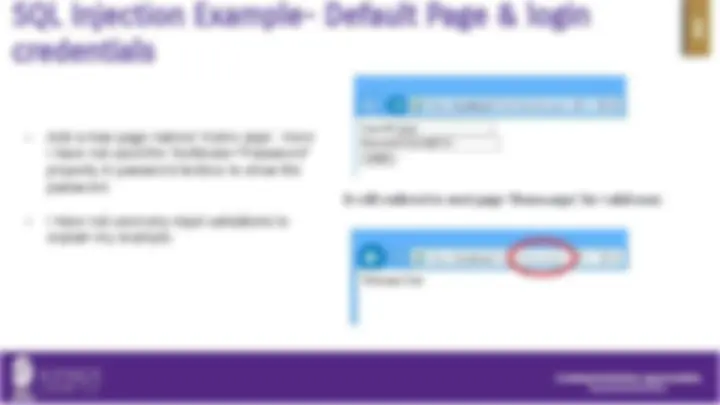
● Now I will create a login page named ‘Default.aspx’ to validate the credentials from the ‘Login’ table and if user is valid then redirect to it to the next page named ‘Home.aspx’.
● Add 2 textboxes for UserID & Password respectively and a button for login.
Search Field
● Add 2 namespaces in the .cs file of the ‘Default.aspx’.
● Now add the following code to validate the credentials from the database on click event of Login button.
KCIC
Search Field
It will redirect to next page ‘Home.aspx’ for valid user.
KCIC
Search Field
It will redirect to next page name ‘Home.aspx’ for valid user.
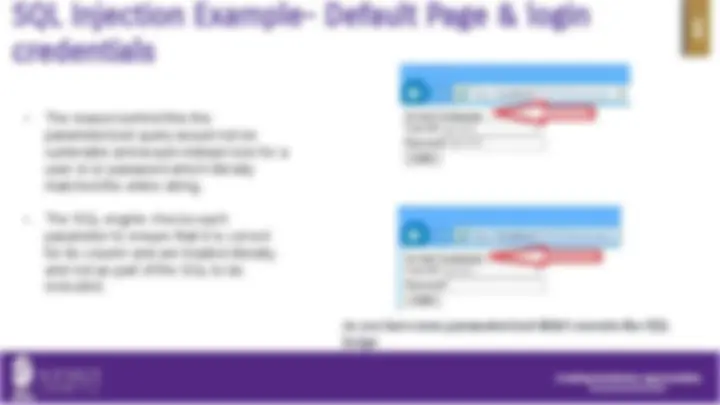
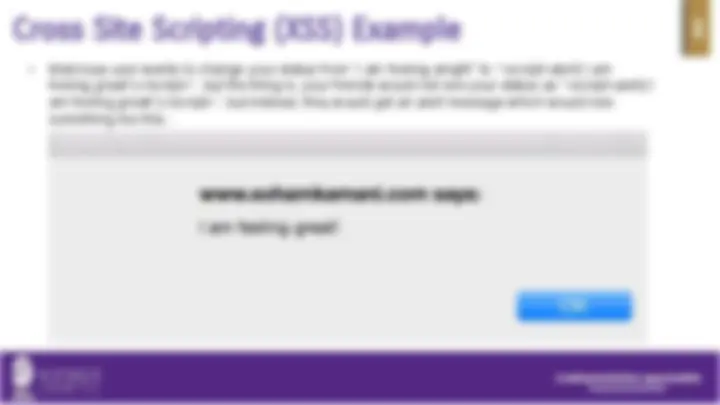
See what happened. This is called SQL injection in the hacking world.
KCIC
Search Field
As you have seen parameterized didn’t execute the SQL Script
Search Field
● A database with a table consisting of username and password columns, passwords can be stored like this:
● The problem 🡪 It is insecure
username password
john myawesomepassword
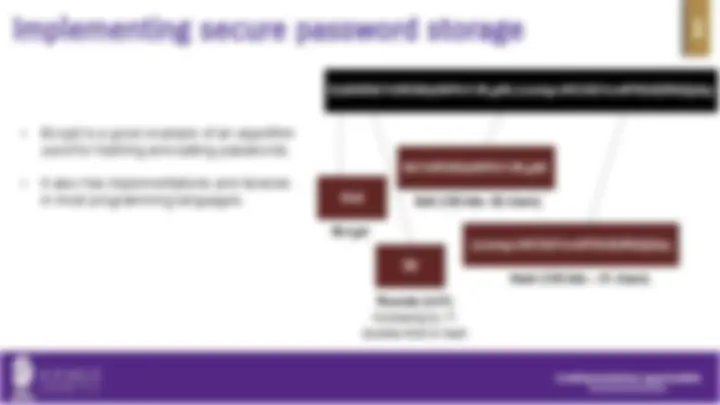
● Use an established hashing algorithm like md5 or sha-1. These hashing algorithms cannot be reversed in theory.
● Every letter of the password with the next letter in the alphabet.
● The problem 🡪 you will find many passwords which are just common words and phrases. Many websites like this one have lookup tables of md5 hashes of common words. This means that if your user set a common word as his password, it can be easily looked up and cracked.
username password
john
3729ad9ab30ed75be1f 2a5f250f07ac
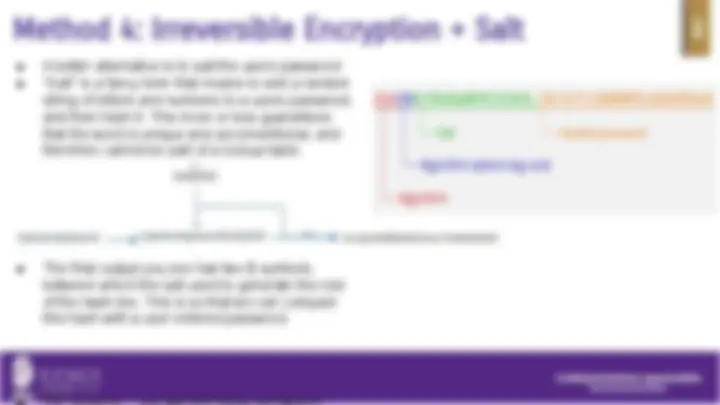
● A better alternative is to salt the users password. ● “Salt” is a fancy term that means to add a random string of letters and numbers to a users password, and then hash it. This more or less guarantees that the word is unique and unconventional, and therefore cannot be part of a lookup table.
● The final output you see has two $ symbols, between which the salt used to generate the rest of the hash lies. This is so that we can compare this hash with a user entered password.