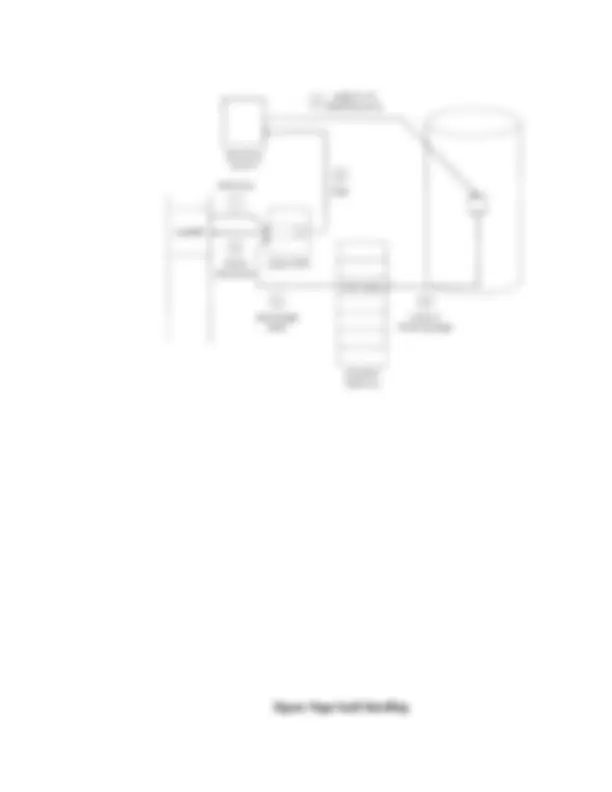
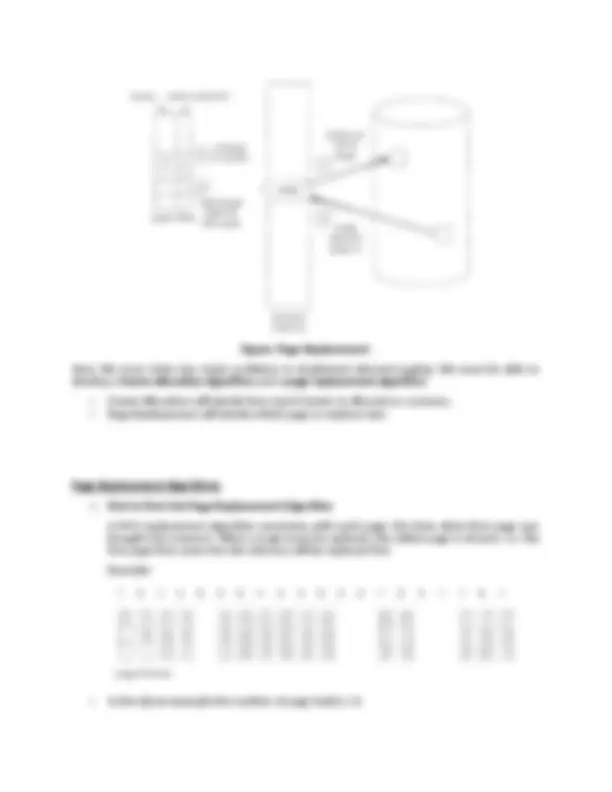
Download Memory Management Techniques: A Comprehensive Guide and more Lecture notes Operating Systems in PDF only on Docsity!
Memory Management
Introduc�on
- The main purpose of a computer system is to execute programs. These programs, together with the data they access, must be at least par�ally in main memory during execution.
- To improve both the u�liza�on of the CPU and the speed of its response to users , a general-purpose computer must keep several processes in memory.
- Memory Management Strategies allocates and deallocates the memory to the processes.
- The main goal of memory management is to increase the u�liza�on of memory by elimina�ng fragmenta�on.
Some important issues per�nent to Memory Management
Need of Cache Memory: Rela�ve speed for accessing physical memory
- Machine instruc�ons o�en takes memory addresses as arguments. Therefore, any instruc�ons in execu�on, and any data being used by the instruc�ons, must be in one of these direct-access storage devices. If the data are not in memory, they must be moved there before the CPU can operate on them.
- Main memory is accessed through a memory bus and comple�ng one memory access can take many cycles of CPU Clock. In such cases, the processor normally needs to stall, since it does not have the data required to complete the instruc�on that it is execu�ng.
- The remedy is to add fast memory between the CPU and main memory called Cache Memory.
Protec�on of Memory Space
Correct opera�on to protect the opera�ng system from access by user processes and, in addi�on, to protect user processes from one another.
- This protec�on is provided by the hardware.
- We need to make sure that each process has a separate memory space.
- A Range of legal addresses needs to be determined that the process may access and to ensure that the process can access only these legal addresses.
- We provide this protec�on by using two registers, usually a base and limit registers.
Figure: Base and a Limit register
- The base register holds the smallest legal physical memory address.
- The limit register specifies the size of the range.
For example, if the base register holds 300040 and the limit register is 120900, then the program can legally access all addresses from 300040 through 420939 (inclusive).
- Protec�on of memory space is accomplished by having the CPU hardware compare every address generated in user mode with the registers.
Figure: Hardware address protec�on with base and limit registers.
- This scheme prevents a user program from (accidentally or deliberately) modifying the code or data structures of either the opera�ng system or other users.
- The base and limit registers can be loaded only by the opera�ng system.
- If execu�on-�me binding is being used, however, then a process can be swapped into a different memory space, because the physical addresses are computed during execu�on �me.
Constraints on Swapping
- If we want to swap a process, we must be sure that it is completely idle.
- We must check out if the process is wai�ng for an I/O or not?
- A process may be wai�ng for an I/0 opera�on when we want to swap that process to free up memory. However, if the I/0 is asynchronously accessing the user memory for I/ 0 buffers, then the process cannot be swapped.
- Assume that the I/0 opera�on is queued because the device is busy. If we were to swap out process P1 and swap in process P2, the I/0 opera�on might then a�empt to use memory that now belongs to process P.
There are two main solu�ons to this problem: never swap a process with pending I/0, or execute I/0 opera�ons only into opera�ng-system buffers. Transfers between opera�ng-system buffers and process memory then occur only when the process is swapped in.
Memory Management Techniques
We use two techniques for memory management: Con�guous Memory Alloca�on and Non- Con�guous Memory Alloca�on.
Con�guous Memory Alloca�on
- In. con�guous memory alloca�on, each process is contained in a single con�guous sec�on of memory.
- It in general provides a fast access to data and are easy to manage.
- Con�guous memory alloca�on suffers from External Fragmenta�on. External fragmenta�on means that the memory is available to be allocated to a process but due to some constraints (not available in con�guous fashion) it cannot be allocated to the process.
- We have two main sub parts to the con�guous memory alloca�on scheme:
- Fixed Par��on Scheme
- Variable Par��on Scheme
Fixed Par��on Scheme
- In fixed par��on scheme the number of par��ons are fixed but the size is not fixed.
- The degree of mul�programming is restricted by the number of par��ons in the memory.
- We cannot re use the allocated par��on even if some memory is s�ll le�.
- Fixed Par��on Scheme suffers from internal fragmenta�on as we have to allocate the en�re par��on to the process even though it requires less memory then the par��on, internal fragmenta�on is wastage of memory. It will always occur due to fixed size partitioning.
Variable Size Par��oning
- In the scheme, the opera�ng system keeps a table indica�ng which parts of memory are available and which are occupied.
- Ini�ally, all memory is available for user processes and is considered one large block of available memory called a hole.
Dynamic Storage alloca�on Problem
It concerns how to sa�sfy a request of size n from a list of all free holes.
Par��on Alloca�on Policies
There are in general three algorithms used to:
- First Fit Algorithm
- Best Fit Algorithm
- Worst Fit Algorithm
First Fit Algorithm
Allocate the first hole that is big enough. Searching can start either at the beginning of the set of holes or at the loca�on where the previous first-fit search ended. We can stop searching as soon as we find a free hole that is large enough.
Best Fit Algorithm
Allocate the smallest hole that is big enough. We must search the en�re list, unless the list is ordered by size. This strategy produces the smallest le�over hole.
Worst Fit Algorithm
Allocate the largest hole. Again, we must search the en�re list, unless it is sorted by size. This strategy produces the largest le�over hole, which may be more useful than the smaller le�over hole from a best-fit approach.
Some simula�on findings
- First fit and best fit are be�er than worst fit in terms of decreasing �me and storage utilization.
- Neither first fit nor best fit is clearly be�er than the other in terms of storage u�liza�on, but first fit is generally faster.
- Best fit performs best in Fixed Size par��oning scheme as the le�overs are small in best fit and vice versa for worst fit.
Basic Method
- The basic method for implemen�ng paging involves breaking physical memory into fixed-sized blocks called Frames and breaking logical memory into blocks of the same size called pages.
Figure: Paging Hardware
- Every address generated the CPU is divided into two parts: a page number (p) and a page offset (d).
- The page number is used as an index into a Page table. Page table is a Data Structure.
- The page table contains the base address of each page in physical memory.
- page table is kept in main memory, and a PTBR (Page Table Base Register) points to the page table.
- Changing page tables requires changing only this one register, substan�ally reducing context-switch �me.
- This base address is combined with the page offset to define the physical memory address that is sent to the memory unit.
Some points to remember
- When we use a paging scheme, we have no external fragmenta�on: any free frame can be allocated to a process that needs it. However, we may have some internal fragmenta�on.
- Most OS allocate a page table for each process.
Problem with Paging
- The problem with this approach is the �me required to access a user memory loca�on. If we want to access loca�on i, we must first index into the page table, using the value in the PTBR offset by the page number for i. This task requires a memory access. It provides us with the frame number, which is combined with the page offset to produce the actual address. We can then access the desired place in memory. With this scheme, two memory accesses are needed to access a byte ( one for the page-table entry, one for the byte ). Thus, memory access is slowed by a factor of 2.
Concepts for Numericals
- 2^10: 1K
- 2^20: 1M
- 2^30: 1G
- 2^40: 1T
- If you have n bits then it will support a memory of: 2^n * Size of the Loca�on (Generally Byte)
- Ex: If we have 14 bits and size of loca�on is 1 B then: 2^14 * 1B = 16 KB
- If you have the memory size and you need to calculate the number of bits required then: Memory Size / 1B (Accordingly)
- Now, to calculate the number of bits: log base 2 n.
Transla�on Look Aside Buffer (TLB)
To solve the problems in paging we take the help of TLB.
- The TLB is associa�ve, high-speed memory.
- Each entry in the TLB consists of two parts: a key (or tag) and a value. When the associa�ve memory is presented with an item, the item is compared with all keys simultaneously. If the item is found, the corresponding value field is returned.
- The search is fast; the hardware, however, is expensive.
- TLB Contains the frequently referred page numbers and corresponding frame number.
The TLB is used with page tables in the following way. The TLB contains only a few of the page- table entries. When a logical address is generated by the CPU, its page number is presented to the TLB. If the page number is found, its frame number is immediately available and is used to access memory. The whole task may take less than 10 percent longer than it would if an unmapped memory reference were used.
Memory Protec�on
- Memory protec�on in a paged environment is accomplished by protec�on bits associated with each frame. Normally, these bits are kept in the page table.
- One bit can define a page to be read-write or read-only.
- One addi�onal bit is generally a�ached to each entry in the page table: a valid-invalid bit.
- When this bit is set to "valid," the associated page is in the process's logical address space and is thus a legal (or valid) page.
- When the bit is set to"invalid," the page is not in the process's logical address space.
- Illegal addresses are trapped by use of the valid -invalid bit.
Figure: Valid Invalid Bits for Memory Protec�on
Problem with such Memory Protec�on
Suppose, for example, that in a system with a 14-bit address space (0 to 16383), we have a program that should use only addresses 0 to 10468. Given a page size of 2 KB. Addresses in pages 0, 1, 2, 3, 4, and 5 are mapped normally through the page table. Any a�empt to generate an address in pages 6 or 7, however, will find that the valid -invalid bit is set to invalid, and the computer will trap to flee opera�ng system (invalid page reference).
No�ce that this scheme has created a problem. Because the program extends only to address 10468, any reference beyond that address is illegal. However references to page 5 are classified as valid, so accesses to addresses up to 12287 are valid. Only the addresses from 12288 to
16383 are invalid. This problem is a result of the 2-KB page size and reflects the internal fragmenta�on of paging.
Solu�on:
- Some systems provide Page Table Length Register (PTLR) hardware, in the form of a length to indicate the size of the page table. value is checked against every logical address to verify that the address is in the valid range for the process.
Mul�level Paging / Hierarchical Paging
- Modern systems supports a large logical address space (2^32 to 2^64).
- In such cases, the page table itself becomes excessively large and can contain millions of entries and can take a lot of space in memory.
- A simple solu�on to this is to divide page table into smaller pieces.
- One way is to use a two-level paging algorithm , in which the page table itself is also paged.
Figure: Two-level Paging
- Consider an example of a 32-bit logical address space and a page size of 4 KB. A logical address is divided into a page number consis�ng of 20 bits and a page offset consis�ng of 12 bits. Because we page the page table, the page number is further divided into a 10- bit page number and a 10-bit page offset. Thus, a logical address is as follows:
- Each entry consists of the virtual address of the page stored in that real memory loca�on, with informa�on about the process that owns the page. Thus, only one page table is in the system, and it has only one entry for each page of physical memory.
- Thus number of entries in the page table is equal to the number of frames in the physical memory.
Figure: Inverted Page Table
- Each inverted page-table entry is a pair <process-id, page-number> where the process-id assumes the role of the address-space iden�fier (ASID).
- (^) An ASID uniquely iden�fies each process and is used to provide address-space protec�on for that process.
- When a memory reference occurs, part of the virtual address, consis�ng of <process-id, page number>, is presented to the memory subsystem. The inverted page table is then searched for a match. If a match is found-say, at entry i-then the physical address <i, offset> is generated. If no match is found, then an illegal address access has been a�empted.
- This scheme decreases the amount of memory needed to store each page table, but it increases the amount of �me needed to search the table when a page reference occurs. Because the inverted page table is sorted by physical address, but lookups occur on virtual addresses, the whole table might need to be searched for a match.
Segmenta�on (h�ps://www.youtube.com/watch?v=dz9Tk6KCMlQ)
- Paging is unable to separate the user's view of memory from the actual physical memory.
- Segmenta�on is a memory-management scheme that supports this user view of memory.
Figure: User View of the Program
- A logical address space is a collection of segments.
- Each segment has a name and a length. The addresses specify both the segment name and the offset within the segment. The user therefore specifies each address by two quan��es: a segment name and an offset.
- Thus, a logical address consists of a two tuple:
<segment-number, offset>.
- (^) Segments can be of variable lengths unlike pages and are stored in main memory.
Segmenta�on Hardware
Figure: Segmenta�on with Paging
Virtual Memory
All the previous strategies have the same goal: to keep many processes in memory simultaneously to allow mul�programming. However, they tend to require that an en�re process be in memory before it can execute.
- Virtual memory is a technique that allows the execu�on of processes that are not completely in memory.
- One major advantage of this scheme is that programs can be larger than physical memory.
- Virtual memory abstracts main memory into an extremely large, uniform array of storage, separa�ng logical memory as viewed by the user from physical memory.
- Virtual memory also allows processes to share files easily and to implement shared memory.
- It provides an efficient mechanism for process crea�on.
- It frees up the concern of memory limita�ons.
Disadvantages
- Virtual memory is not easy to implement.
- It may substan�ally decrease performance if it is used carelessly
T
here are many instances where a program is seldom executed so there is no need to keep those programs in memory as it limits the size of a program to the size of physical memory.
The ability to execute a program that is only par�ally in memory would confer many benefits:
- A program would no longer be constrained by the amount of physical memory that is available.
- More programs could be run at the same �me as use of physical memory is less.
- Less I/O would be needed to load or swap user programs into memory, so each user program would run faster.
Figure: Virtual Memory
Demand Paging
- With demand-paged virtual memory, pages are only loaded when they are demanded during program execu�on; pages that are never accessed are thus never loaded into physical memory.
- A demand-paging system is similar to a paging system with swapping where processes reside in secondary memory (usually a disk). When we want to execute a process, we swap it into memory.
- But rather than swapping the en�re process into memory, we use a Lazy Swapper. A lazy swapper never swaps a page into memory unless that page will be needed.
- We use the term Pager instead of swapper in demand paging.
Basic Concepts
- When a process is to be swapped in, the pager guesses which pages will be used before the process is swapped out again. Instead of swapping in a whole process, the pager brings only those pages into memory.
- Thus, it avoids reading into memory pages that will not be used anyway, decreasing the swap �me and the amount of physical memory needed.
- Now we need some hardware to dis�nguish between which pages are in memory and which are not, so The valid -invalid bit scheme can be used for it.
Figure: Page Fault Handling
- Pure Demand Paging: In the extreme case, we can start execu�ng a process with no pages in memory. When the opera�ng system sets the instruc�on pointer to the first instruc�on of the process, which is on a non-memory-resident page, the process immediately faults for the page. A�er this page is brought into memory, the process con�nues to execute, faul�ng as necessary un�l every page that it needs is in memory. At that it can execute with no more faults. This scheme is Pure Demand Paging: never bring a page into memory un�l it is required.
- The Locality of Reference helps Demand Paging in performing reasonably.
- The hardware to support demand paging:
- Page table
- Secondary memory
- A crucial requirement for demand paging is the ability to restart any instruc�on a�er a page fault. Because we save the state (registers, condi�on code, instruc�on counter) of the interrupted process when a page fault occurs, we must be able to restart the process in exactly the same place and state.
Performance of Demand Paging
- Effec�ve Access �me for Demand Paging: (1 - p) x ma + p x page fault service �me.
- Here, p: Page fault rate or probability of a page fault.
- (^) ma is memory access �me.
Page Replacement
With the increase in mul�programming the rate of page faults may rise, thus to reduce the degree of mul�programming the opera�ng system swaps out processes from the memory freeing the frames and thus the process that requires to execute can now execute.
- If no frames are free, two page transfers (one out and one in) are required.
- This situa�on effec�vely doubles the page-fault service �me and increases the effec�ve access �me accordingly.
- We can reduce this overhead by using a Modify bit or Dirty Bit. When this scheme is used, each page or frame has a modify bit associated with it in the hardware.
- The modify bit for a page is set by the hardware whenever any word or byte in the page is wri�en into, indica�ng that the page has been modified.
- If the bit is set : the page has been modified since it was read in from the disk. In this case, we must write the page to the disk.
- If the modify bit is not set , however, the page has not been modified since it was read into memory. In this case, we need not write the memory page to the disk: it is already there.