




































































Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Everything about operating system
Typology: Essays (university)
1 / 168

This page cannot be seen from the preview
Don't miss anything!





























































































Steven Hand
12 lectures for CST IA^ Michaelmas Term 2010
Operating Systems — N/H/MWF@
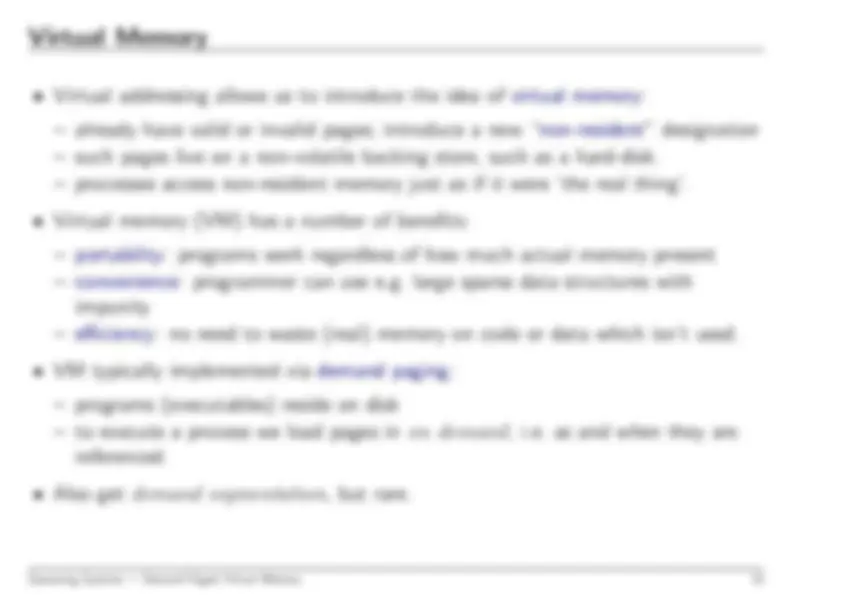
Operating Systems — Aims
i
Operating Systems — Books
iii
Operating Systems — Introduction
1
1949: First stored-program machine (EDSAC)
to
1955: “Open Shop”.
large machines with vacuum tubes.
I/O by paper tape / punch cards.
user = programmer = operator.
To reduce cost, hire an
operator
programmers write programs and submit tape/cards to operator.
operator feeds cards, collects output from printer.
Management like it.
Programmers hate it.
Operators hate it.
need something better.
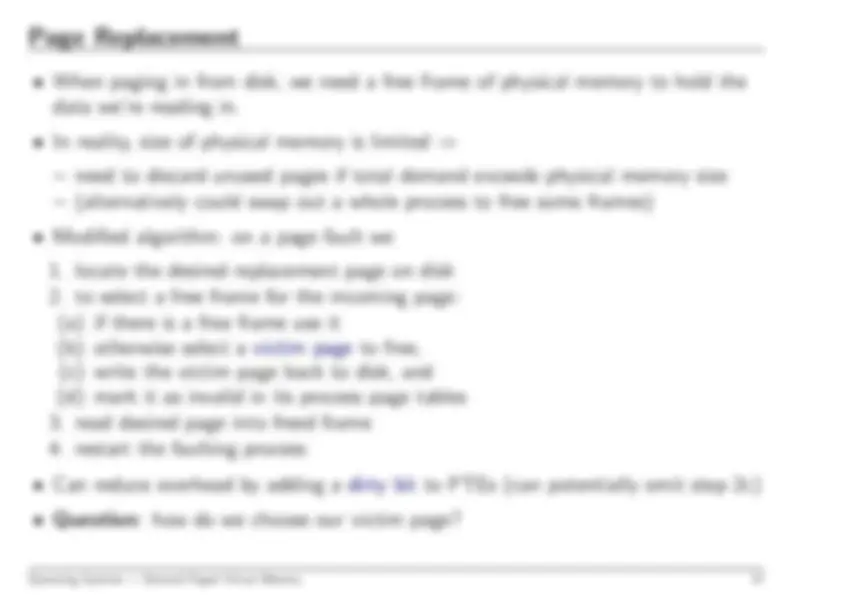
Operating Systems — Evolution
3
Introduction of tape drives allow
batching
of jobs:
programmers put jobs on cards as before.
all cards read onto a tape.
operator carries input tape to computer.
results written to output tape.
output tape taken to printer.
Computer now has a
resident monitor
initially control is in monitor.
monitor reads job and transfer control.
at end of job, control transfers back to monitor.
Even better:
spooling systems
use interrupt driven I/O.
use magnetic disk to cache input tape.
fire operator.
Monitor now
schedules
jobs...
Operating Systems — Evolution
4
personal computers.
no other users
ignore protection.
e.g. DOS, Windows, Win 95/98,...
hard-real time: nuclear reactor safety monitor.
soft-real time: mp3 player.
SMP: 2–8 processors in a box.
MIMD: super-computing.
Java: the network is the computer.
Clustering: the network is the bus.
CORBA: the computer is the network.
.NET: the network is an enabling framework...
Operating Systems — Evolution
6
H/WS/W
App.
App.
App.
Scheduler
Device Driver
Device Driver
App.
Oldest kind of OS structure (“modern” examples are DOS, original MacOS)
trash OS software.
trash another application.
hoard CPU time.
abuse I/O devices.
etc...
No good for fault containment (or multi-user).
Need a better solution...
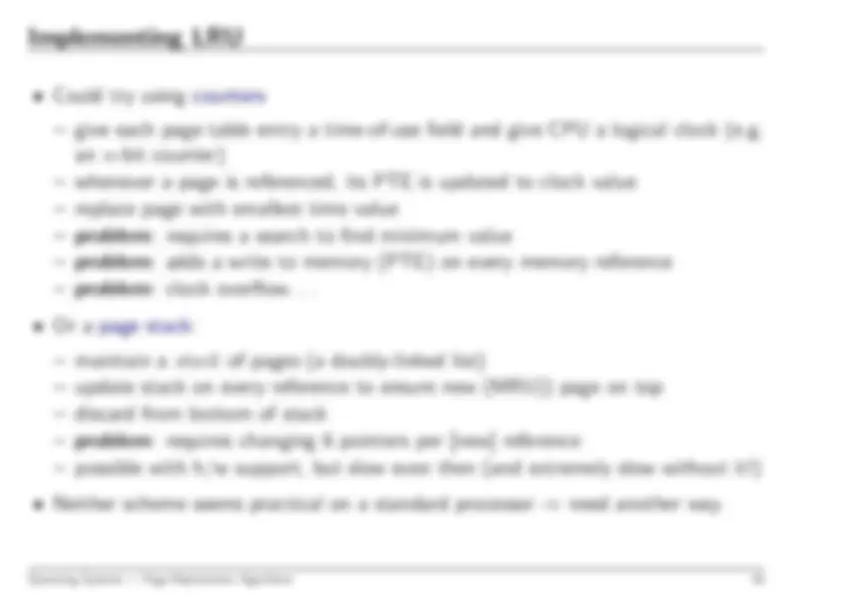
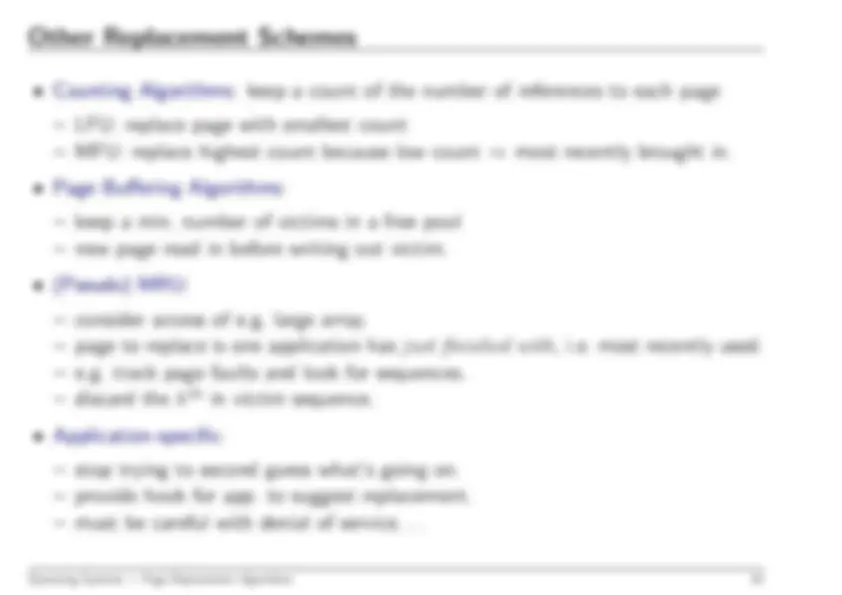
Operating Systems — Structures & Protection Mechanisms
7
applications can’t mask interrupts.
applications can’t control I/O devices.
memory
Hence need to protect memory also, e.g. define
base
and
limit
for each program:
Operating System Job
1
Job
2
Job
3
Job
4
0x00000x30000x50000x98000xD8000xFFFF
0x50000x
base register limit register
Accesses outside allowed range are protected.
Operating Systems — Structures & Protection Mechanisms
9
vector to OS (address error)
yes
no
yes
no
base
base+limit
Memory
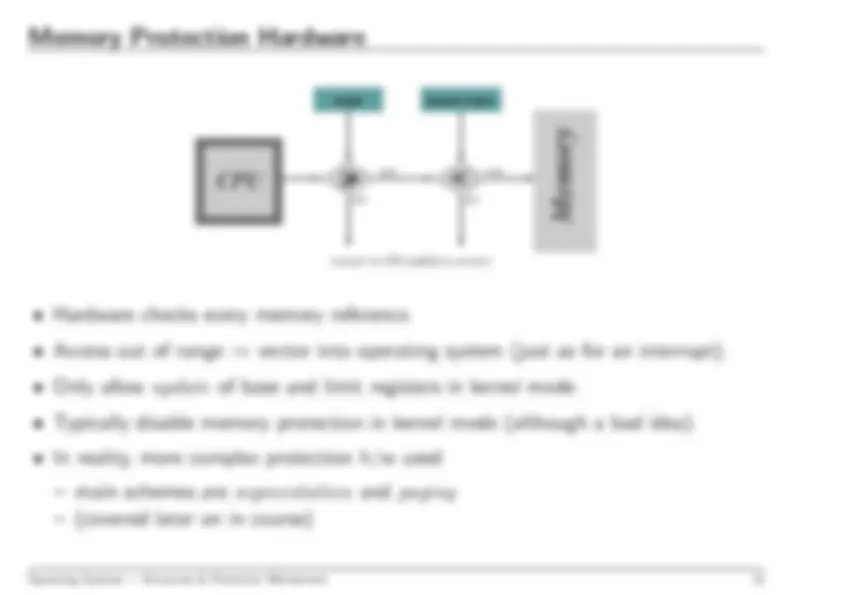
Hardware checks every memory reference.
Access out of range
vector into operating system (just as for an interrupt).
Only allow
update
of base and limit registers in kernel mode.
Typically disable memory protection in kernel mode (although a bad idea).
main schemes are
segmentation
and
paging
(covered later on in course)
Operating Systems — Structures & Protection Mechanisms
10
H/WS/W
App.
PrivUnpriv
App.
App.
App.
Kernel
Scheduler
Device Driver
Device Driver
System Calls
File System
Protocol Code
Applications can’t do I/O due to protection
operating system does it on their behalf.
Need secure way for application to invoke operating system:
kernel mode.require a special (unprivileged) instruction to allow transition from user to
Generally called a
software interrupt
since operates similarly to a real (hardware)
interrupt...
Set of OS services accessible via software interrupt mechanism called
system calls
Operating Systems — Structures & Protection Mechanisms
12
H/WS/W
App.
PrivUnpriv
Server
DriverDevice
Server
Server
App.
App.
App.
Kernel
Scheduler
Driver^ Device
push some OS services into
servers
servers may be privileged (i.e. operate in kernel mode).
Increases both
modularity
and
extensibility
Still access kernel via system calls, but need new way to access servers:
interprocess communication (IPC) schemes.
Operating Systems — Structures & Protection Mechanisms
13
Operating Systems — Functions
15
on batch system, refer to
jobs
on interactive system, refer to
processes
(we’ll use both terms fairly interchangeably)
Process
Program:
a program is
static
, while a process is
dynamic
in fact, a process
a program in execution
(Note: “program” here is pretty low level, i.e. native machine code or
executable
program counter
stack
data section
Processes execute on
virtual processors
Operating Systems — Processes
16