

































Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
The design and implementation of a system to detect and jam drones in restricted airspace using Software Defined Radios (SDRs) and Recursive Least Squares (RLS) algorithms. The system locates unwanted drones or drone pilots by recording signal strength at different locations and processing the data to find the signal's received signal strength (RSS). The RSS data is then used to calculate the distance between the access point (SDR) and the object (drone/drone pilot). The system also includes a jamming assembly that uses barrage jamming to disrupt the communication between the drone and its controller. details on the hardware and software configurations, frequency considerations, and signal processing techniques used in the system.
Typology: Summaries
1 / 41

This page cannot be seen from the preview
Don't miss anything!


































Nicholas Cauley Ryan Crowley Mara Pranter Advisor: Professor Kaveh Pahlavan December 10th, 2020
With the cost of drones decreasing and their presence in the world increasing, there needs to be a way to control their presence in restricted airspace. To solve this problem, our team designed an assembly to both locate an unwanted drone or drone pilot and jam the communication between drone and the drone controller. First the location was discovered using several SDRs to record signal strength at different locations. This would find either the drone or drone controller when other signals were not present on the same bandwidth. The SDR signal data was then processed to get the signal’s received signal strength (RSS) These results were then mathematically modeled with the path loss model, which turned the RSS values into a distance in meters. Then the recursive least squares algorithm transformed the distances from each SDR into a position in the space that corresponds to the drone or drone controller. Finally, the Cramer Rao Lower Bound was used to estimate the amount of error possible in the position estimation. The jamming was achieved using a microcontroller to broadcast white Gaussian noise at the same frequency as the drone communication to render that communication useless. The location determining system was found to be within a meter of error on the xy plane, however, it had more error on the z axis as the SDRs were not at different enough z positions to sense the z position as accurately. The jamming system was designed and built using analog RF components, fed by voltages from the microcontroller. The effectiveness of the jamming system could not be fully tested as strict COVID-19 protocols limited access to diagnostic equipment.
Drones, also known as unmanned aerial vehicles (UAVs), are becoming more and more accessible as the market for them grows. In 2019, The Federal Aviation Administration (FAA) estimated that there were over 1.25 million drones flying in America, and they predict this number only will increase.^1 This market growth has led to drones in general becoming cheaper to buy, as well as the expected capabilities of them to rise. This combination of lower cost, higher performance and availability is good for the consumer, but poses a massive risk as an increasing number of pilots, out of either negligence or maliciousness, are flying in restricted airspaces around the world. This is a massive safety concern, as it could lead to drones interfering with aircraft, potentially causing deadly crashes.^2 In 2017, a flight near Jean Lesage Airport in Canada collided with a drone.^3 While tragedy was avoided in this incident, the potential for a disaster still looms. Due to the immense risk, airports likely shut down if a drone is flying nearby, possibly causing millions in damages for the airport and its travelers. In 2018, Gatwick Airport in the United Kingdom was shut down for a period of three days. It is estimated that this caused over $1.8 million in damages to the airport, not including the damages of passengers whose flights were delayed or canceled.^4 There is a great need to create a system to prevent all of this damage from occurring. 1.1. Project Description All of this damage can be easily caused with any consumer available drone. Our project is a system that can be implemented in airports, among other areas where drones should not be, to prevent the flying of drones in an area and locate the position of the pilot. Our project is an assembly of systems to locate a drone or its controller, and then jam the signals, preventing the drone from being operated.In the past, a WPI student team created and tested an Adversary UAV Localization system.^5 Their work was used as a starting point for our project. The testing done in the previous project used a cellphone as a substitute for the drone signal. We improved their testing methodology by using a drone controller, providing a more realistic scenario. The biggest improvement on the past project is our addition of a jamming system, allowing the user of the assembly to prevent the drone from flying if it is located in restricted airspace. Our project's localization system finds the location of the drone or its controller by reading the signal strength with several receivers. Once the location of the drone is established, if it is determined that it should be jammed, the jamming system will generate a signal that overwhelms the drone and its controller’s communication, causing the drone to cease flight. A block diagram and general overview diagram can be found in Section 3, System Architecture in Figures 3.1 and 3.2. 1.2. Report Outline This report is broken up into several main sections to aid the reader in understanding the various components and parts of our project. Section 2, Theoretical Background discusses the knowledge and theoretical information required for the reader to understand the detailed workings of the system. Section 3, System Architecture lays out the specific configurations of hardware and software that are used to receive, process, and jam drone signals. Section 4, Results and Discussion explains the processes used to test the system, and then analyzes the results of the tests. Section 5, Conclusions and Future Recommendations goes over the analyzed results, discussing what about our system worked and where it can be improved. Section 5 also gives recommendations for future advancements of this project.
In this section, the theoretical background needed to create and understand this project is discussed. The first subsection discusses the theory behind localization of signals, specifically how they are received, processed, and the various equations, algorithms, and models that go along with it. The second subsection will provide background on the processes of jamming signals, from both a hardware and software perspective. 2.1. Localization In order to best locate either the drone or the drone pilot there are four steps; finding the received signal strength (RSS), the path loss model, recursive least squares (RLS) algorithm, and error analysis. The received signal strength is put into the path loss model which calculates the distance between an access point (SDR) and the object (drone/drone pilot). Once there are calculated distances from each access point to the object, the RLS algorithm is used to position where in a 3D space the object is. Finally, the amount of error possible is estimated with the Cramer Rao Lower Bound (CRLB). 2.1.1. Signal Processing Signal processing gives the RSS to begin the process of mathematically determining the location of the drone or drone pilot. In order to process the signals, one must first read the signal with a software-defined radio (SDR), The SDR itself can not process the signals; it depends on software from a separate device to process signals. The different levels of software that can process signals for SDRs are host, embedded, and programmable logic programs. For the purpose of the localization assembly, GNU Radio, an open source software that runs on the host level was selected due to its high level of documentation in this and similar use cases. GNU Radio allows the user to process signals by making a flowgraph of different signal processing blocks. This flowgraph then generates a Python script that can be run to process live signals from the SDR. Since GNU Radio is a host level software, it must be run on a computer connected to the SDR over an ethernet cord. An important part of the system is having several SDRs in different positions, all reading signals that get processed into RSS values by the host computer. To connect the several SDRs to one computer, a network switch can be used to join the SDRs together before connecting them with the computer. 2.1.2 Localization Setup The physical setup of the localization system is heavily based on the system created by the Adversary UAV Localization project’s team.^5 Their configuration can be described as several SDRs placed in different locations, all connected to a host computer. This setup allows the SDRs to get different RSS values from the same signal, allowing for a localization algorithm to locate the signal source. Our configuration is similar, pictured later in Section 4.1, Figure 4.1. The key part in both configurations is different locations of the SDRs, which allows for the aforementioned different RSS values. The more varied their positions, the more accurate our localization can be.
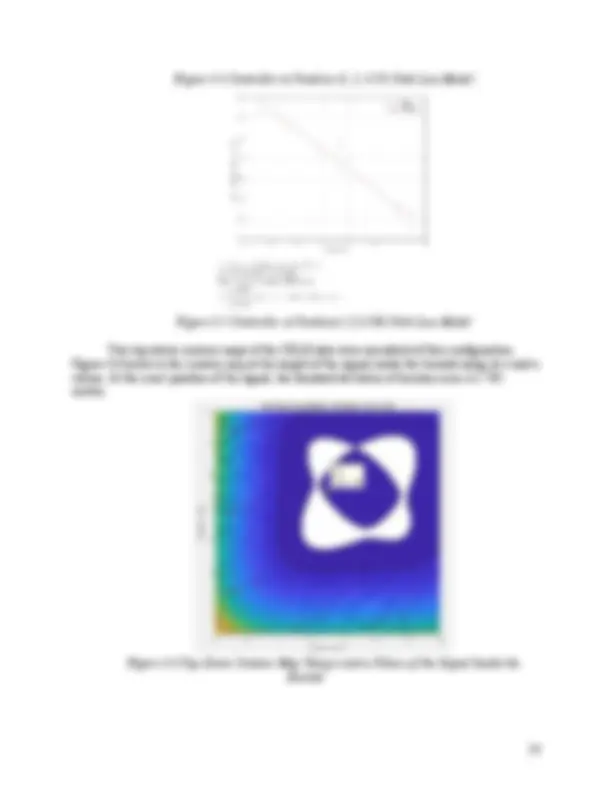
unfortunately in the real world as well as this application these distances are not entirely accurate. This means there needs to be an estimation of the position, this is done with the recursive least squares (RLS) algorithm. This is a method by which to minimize error by guessing a best fit and seeing how great the error squared is. Then the position where this error is the lowest is where the object is assumed to be. This can be demonstrated in two dimensions in the figure below. Figure 2.2 RLS Algorithm in a 2D Space In this team’s application the algorithm is moved into a 3D space, this means the circles are spheres and there needs to be four access points in order to estimate the object’s z position. 2.1.5. CRLB Error Analysis in 2D To analyze the potential error of the localization system’s configuration, the Cramer Rao Lower Bound (CRLB) was calculated. CRLB is the theoretical minimum variance of a system. In the case of a localization system, it gives the standard deviation of localization error at a point in space. The lower the CRLB value is, the less likely it is for the system to have high error at that point. Calculating the CRLB for an entire space of points is important to get an estimate on the error of the system configuration. The equation for the CRLB in this localization system for 2D is derived from equation 2.1, the path loss model. First the distance for each point from the SDR is calculated. This is repeated for each SDR in the system. The equation used is:
2
2 The distance power gradient, α, is a constant calculated in the path loss model shown in section 2.1.2. It is multiplied by another distance based calculation that uses the distance, r, calculated in equation 2.3. This entire calculation is repeated for each dimension, twice in the case of a 2D space, for each SDR. The entire equation is:
2 These two arrays are then combined into a single matrix, H. The covariance matrix is then created using H and σ, the standard deviation of shadow fading found in the path loss model. The equation for this is:
2
− The covariance matrix now contains the covariance of each point’s location error, σ^2 x and σ^2 y. To find the standard deviation of the location error for a point, the CRLB, the following equation is used:
2
2 y 2.1.6. CRLB Error Analysis in 3D While the previous set of equations finds the CRLB in a 2D space, the localization system being implemented needs to work in 3D space. To accomplish this, another dimension was added to the equations. The 3D version of equation 2.3 is:
2
2
2 Similarly, the 3D versions of the H matrix equations are as follows:
2
2
2 The covariance matrix equation, 2.6, still works in 3D space with no modifications. The result does slightly change however. It still contains the covariances of each point’s location
as it accounts for the new dimension in the covariance matrix, as shown below:
2
2
2 z The result of these 3D equations is the standard deviation of location error in 3D space. To find the CRLB for every point in 3D space, a MATLAB script using the 3D CRLB equations was used to automate the process. 2.2. Jamming
Table 2.2: Frequencies used for Video by Common Drone Brands^7 One major outcome from Table 2.2 is that the video link is often done through the 5. GHz band or 2.4 GHz band. Therefore, based on the results from these two tables, as well as some further research completed on drone brands and their frequencies, this project has determined that jamming the 2.4 GHz band will be sufficient for this application. A simple bandpass filter for the 2.4-2.5 GHz band will allow for the jamming assembly to only process signals within this band. This will be further detailed in Chapter 3, System Architecture. 2.2.2 Jamming Scenario In order to understand the hardware and software that is necessary for a drone jamming assembly, it is important to first design and analyze a block diagram which shows each step in the process from the reception of a signal to the transmission of a high power signal meant to jam the drone’s communication with its controller. As identified in Section 2.2.1 the common drone frequencies which will be taken into account in the drone jamming assembly is 2.4 GHz. Shown below in Figure 2.1 is a top-level block diagram of how the RF drone jamming assembly will be designed to operate. Yuneec 5.8 GHz Connex 5.8 GHz Boscam 5.8 GHz
Figure 2.3: Drone Jamming Block Diagram The first part of the drone jamming assembly, the 2.0 to 6.0 GHz antenna, is used to both receive and transmit RF signals. The reason for the 2.0 to 6.0 GHz range is because this range covers all received signals to be analyzed.It is important that the antenna be able to perform both signal reception and transmission because when it is determined that a received signal is within either of the frequency ranges that needs to be jammed, a high power signal of the same frequency will be emitted to confuse the drone. In order for this to be accomplished, there needs to be a switch which transitions between the receive and transmit operation of the antenna. This switch will be controlled by the microcontroller. When the microcontroller is used in the receive mode, all signals received through the antenna will be sent to a Low Noise Amplifier. The purpose of this amplifier in the block diagram is to amplify any low-power signals while maintaining a negligent change to its signal-to-noise ratio. This electrical component amplifies the power of the signal while adding minimal amounts of noise to the system. This allows for received signals that are low in power to be more easily processed and analyzed at later components of the RF jamming assembly in Figure 2.1. A Detector Logarithmic Video Amplifier (DLVA) will be the next electrical component that takes in the RF signal. A DLVA converts the energy of the RF signal into a Direct Current (DC) Voltage (the detector portion), and then amplifies the signal through an amplifier with a logarithmic transfer function (the logarithmic video amplifier portion). By relating the RF power of each bandpass filter to a specific DC Voltage, the microcontroller can then determine if the signals are significant enough to be an actual drone signal as opposed to noise. This part in the process is crucial, as it links the RF signals to information that the microcontroller can process. The electrical component which will receive this outputted Voltage is a Voltage Controlled Oscillator (VCO). A VCO takes a specific DC Voltage input and produces an RF signal output that is determined by the Voltage of the input. The purpose of this electrical component is to allow for the microcontroller to send out a 2.4 GHz signal that will eventually be transmitted through the antenna. This ensures that the signal sent out matches the frequency of the signal it wishes to jam. Lastly, a High Power Amplifier will amplify the power of the RF signal outputted by the VCO. This electrical component ensures that the signal is of a high enough power to adequately jam the drone’s signals. If the power of the signal outputted by the jamming system is not significant enough, then the drone will still be able to communicate with its host controller without significant interruption. If the RF transmit/receive switch is turned to transmit mode, this high power signal will then be sent out to the surrounding environment through the antenna. This process will be followed whenever the jamming assembly is powered on. 2.2.3 Software Considerations The barrage jamming technique was selected to be the method by which to jam the drone communication because it is able to fill an entire band of communication with noise making communication impossible. The barrage jamming technique is particularly useful as many drones will change frequencies as communication drops and some have complex linking procedures.^8 The one possible problem with barrage jamming is that as the signal is spread over a band it loses strength. This is able to be countered by making sure the power is greater from the jammer
The overall system is broken into two main parts. First there is the location system which is responsible for finding either the drone or drone pilot. This is done with software defined radios (SDRs) which return the received signal strength which can then be mathematically transformed into a position in a 3D space. The second part of the system is the jamming device which uses barrage jamming software on a microcontroller and RF hardware to disrupt the signal between the drone controller and the drone. These systems are demonstrated visually below. Figure 3.1 Assembly Block Diagram Figure 3.2 General Systems Overview
3.1. Hardware Modules The categories of hardware used in the assembly can be grouped into three sections: localization, the microcontroller, and jamming. The localization hardware group contains the components used in receiving and processing the signals, and locating their source. The microcontroller links the localization and jamming systems together, feeding the jamming system appropriate voltages to match the signals frequency. The jamming group of components includes the RF hardware that makes up the jamming signal generating circuit. 3.1.1. Localization Components The localization portion of the system uses various hardware to read and process the hardware. Figure 2.1 below shows an overview of the components and connections of the hardware used in the localization system. Figure 3.3 Localization Hardware Overview Diagram (power cords not shown) The system is made up of 4 radios connected by a network switch by ethernet cables. A laptop that is running signal processing software is also connected to the switch, Not pictured in the diagram are the power strip and extension cords used to get power to the radios and switch. 3.1.2. Microcontroller A microcontroller, allows this project to best accomplish the digital processing and creation of signals. This is because microcontrollers are fast and can easily be integrated with other circuitry. The microcontroller will be responsible for the following: ❖ Switching the antenna between receiving and transmitting ❖ Taking voltages from the RF circuits and converting it into digital data ❖ Filter noise ❖ Create a jamming signal and send the signal to the transmission portion of the RF circuit The details of how these tasks are tackled in the coding of the microcontroller is explored later in the Section 3.3 of this paper. The microcontroller being used is the Arduino MKR 1010. Below is a diagram of the board’s main components.
Table 3.1: Component Voltage and Current Requirements All ordered components can be powered by a 5V DC supply, which gives us the availability to power the entire circuit on one 5V power source. The total current required by all components (excluding the Arduino) is 354.5 mA, which can be powered by a USB cord connected to a laptop, which supplies 5V at 500 mA. The final conclusion from Table 3.1 is that all RF components can be powered by a single external laptop, with one USB cord powering and controlling the Arduino, and another powering all of the active RF components. Another consideration with respect to the ordered RF components is the RF specifications of each part. Table 3.1 highlights each of the main specifications of each component. Table 3.2: Component Specifications The one common specification of all RF components in the jamming assembly is the frequency range of each. As shown in Table 3.2 above, all components meet the desired jamming range of 2400 MHz to 2500 MHz. This means that all components throughout the assembly will be able to properly operate within the desired band.
3.2. Software Modules 3.2.1. Receiving and Processing As mentioned in section 2.1.1, to receive and process signals using SDRs a software is needed. The software used in this system is GNU Radio, ran on a host computer connected to the radios over ethernet. The GNU Radio flowgraph shown below in Figure 3.3 uses the SDR as a receiver tuned to a frequency range of about 2.4 - 2.45 GHz. It then takes the incoming signals, squares their magnitude, and uses that value in a logarithmic function to find the RSS. The flowgraph then writes the RSS to a log file, resulting in millions of data points in just a few seconds. This flowgraph was then repeated for the three remaining SDRs, each with their own log file. After generating and running the script from the flowgraph, a separate Python script was created to average the millions of RSS values for each SDR. Figure 3.5 GNU Radio Flowgraph to find RSS of Incoming Signals These scripts were used on the host laptop in the configuration shown in Figure 3.2. This connects the software to the localization hardware, completing the localization system. 3.2.2. Jamming The software has various roles to fulfill in the jamming section of this project, these tasks are listed in the 3.1.1. microcontroller section of this paper. First switching the antenna between receiving and transmitting in order to both read the signal to the drone then properly jam it. The readings should then be processed into a digital format to work with. The data is then cleaned of any noise to isolate the important communication signal. Finally a pseudo-random signal, the barrage jamming noise, is created to be broadcasted and jam the communication to the drone.