



Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Here in the documents all the essential basics of the burp suite have been explained .
Typology: Summaries
1 / 7

This page cannot be seen from the preview
Don't miss anything!




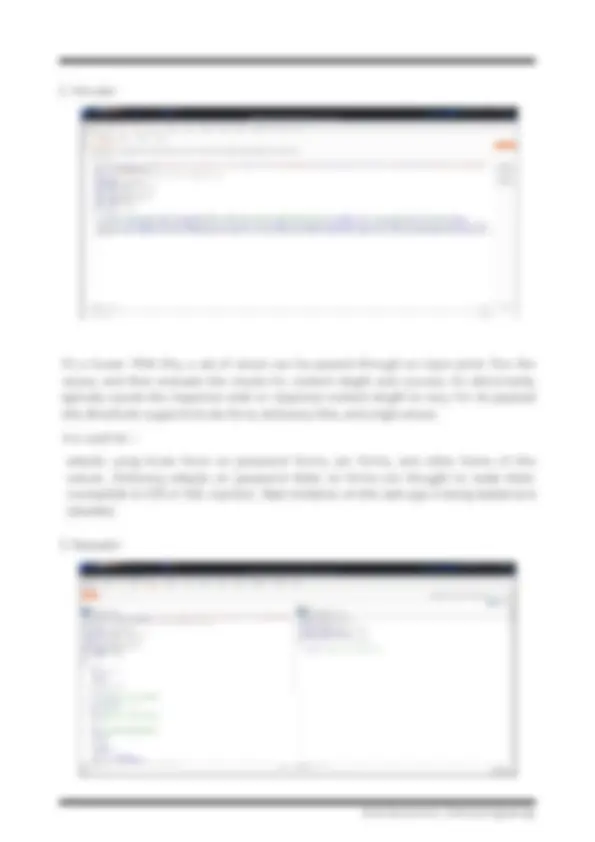
Burp Suite Functionalities Burp Suite is a fully functional web application attack tool that can be used to conduct practically any type of penetration test on a website. The capability of Burp Suite to intercept HTTP requests is one of its key features. Typically, HTTP requests are transmitted directly from your browser to a web server, where they are answered, and then returned to your browser. However, with Burp Suite, HTTP requests are sent directly from your browser to Burp Suite, which then snoops on the traffic. This is what the dashboard of the Burp Suite looks like. We need to set up the Burp suite by Installing the CA Certificate of burp into the browsers trusted certificate list, so that the Burp can easily intercept the incoming and the outgoing traffic. Also we need to set the host address as 127.0.0.1 and the istening port to 8080. It is created by the company Portswigger, whose creator Dafydd Stuttard also goes by that title. BurpSuite is designed to be an all-in-one toolkit, and BApps are add-ons that may be installed to expand its functionality. Week 2
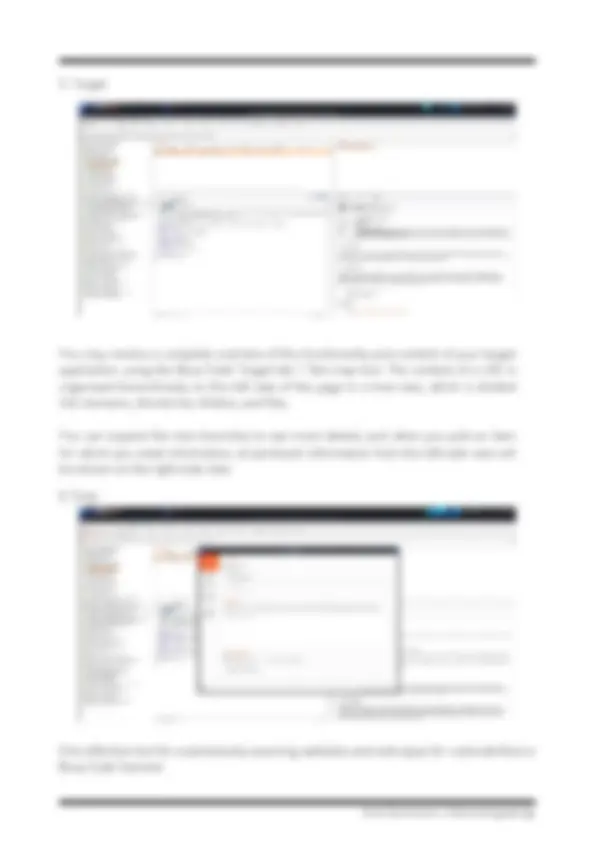
Burp Suite has an inbuilt vulnerability scanner which tries to detect the vulns on it's own whenever it intercepts the packets. In the above image we can see it clearly shows what problem has been found and where it has bee found. Also it categorises the vulnerabilities on the basis of their critical level. It shows the host name and the path where we need to go down to find the problem.
Burp Repeater is a straightforward tool for manually altering, reissuing, and examining the replies from the application to individual HTTP requests. Anywhere in Burp allows you to send a request to Repeater, edit it, then send it repeatedly. Repeater is made to accept your requests and allow you to alter and replay them whenever you like. It is an extremely helpful tool for adjusting and enhancing payloads intended to take advantage of SQL injection or cross-site scripting vulnerabilities, often known as XSS and SQLI, respectively.